Vision
As the leading voice on the policies and principles of open source, the OSI helps build a world where the freedoms and opportunities of open source software can be enjoyed by all. The OSI supports institutions and individuals working together to create communities of practice in which the healthy open source ecosystem thrives.
Mission
The Open Source Initiative (OSI) is a non-profit corporation with global scope formed to educate about and advocate for the benefits of open source and to build bridges among different constituencies in the open source community.
Open source enables a development method for software that harnesses the power of distributed peer review and transparency of process. The promise of open source is higher quality, better reliability, greater flexibility, lower cost, and an end to predatory vendor lock-in.
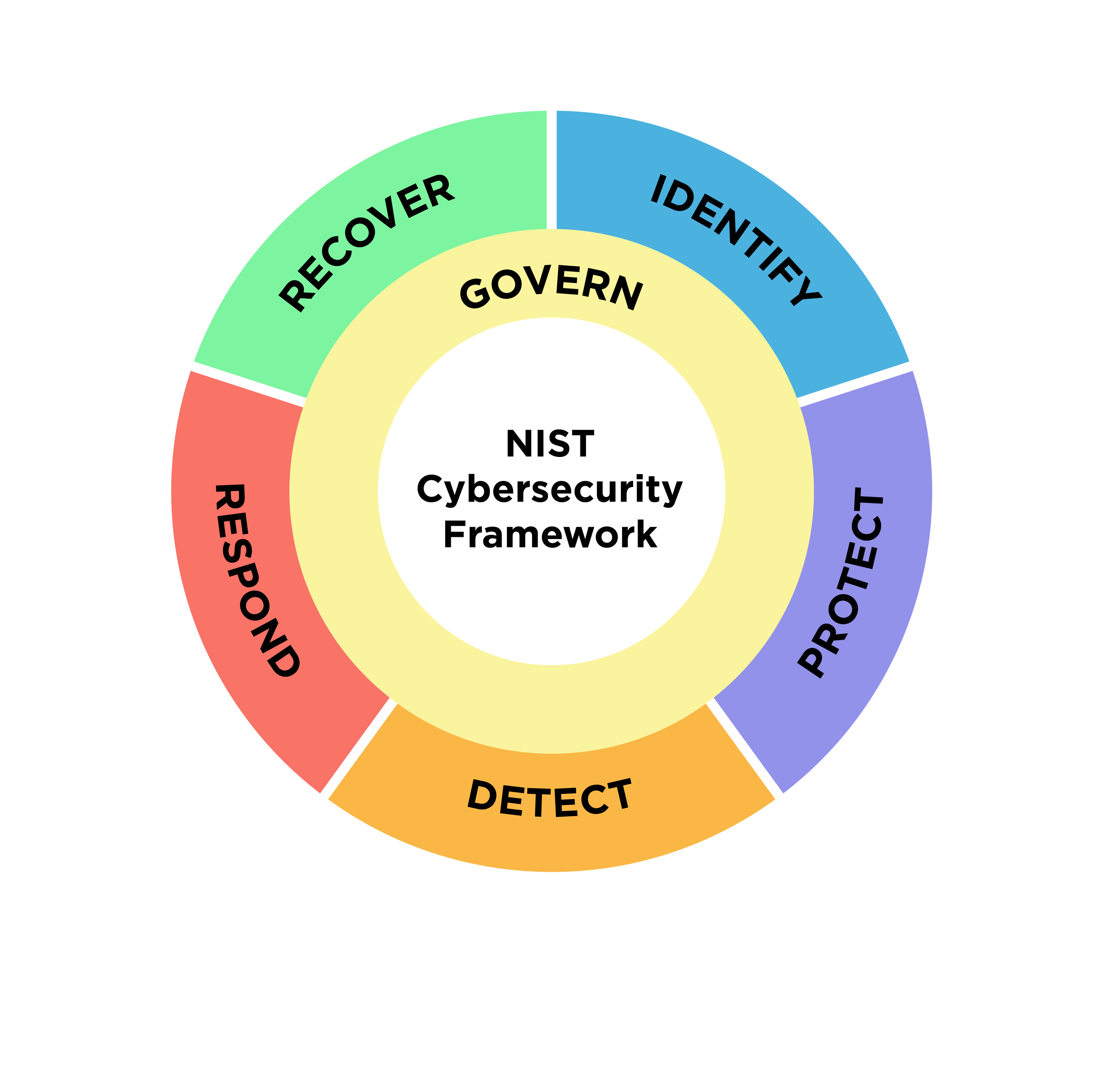
One of our most important activities is as a standards body, maintaining the Open Source Definition for the good of the community. The Open Source Initiative Approved License trademark and program creates a nexus of trust around which developers, users, corporations and governments can organize open source cooperation.